CRD #10
On ransomware and workforce trends, passkey adoption and effects of API sprawl.

The Cybersecurity Research Digest cuts through the bias and marketing fluff to bring you relevant and objective insights backed by data.
Featuring validated research highlights from sources released between 29 October and 4 November 2024, followed by a list of all monitored reports.
Ransomware in 2024: RansomHub's dominance, remote encryption & more data exfiltration
Recent cyber threat intelligence reports indicate that RansomHub has emerged as a dominant force in the ransomware ecosystem in 2024, responsible for approximately a fifth of publicly disclosed victims in September 2024. The group employs advanced tactics, notably remote encryption, which contrasts with traditional local encryption methods that are more easily detected and mitigated.
The lates data also confirms the growing trend among threat actors to leverage data exfiltration and the threat of public leaks as extortion tactics, moving away from solely relying on data encryption.
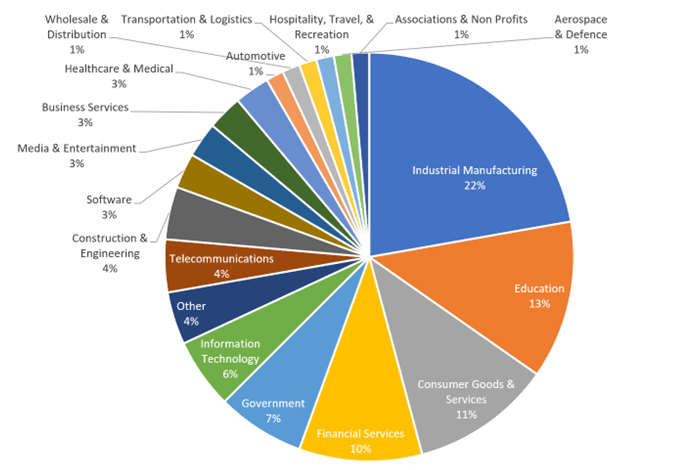
Industrial manufacturing remains the most targeted sector, primarily due to its reliance on legacy systems, the challenging integration of IT and OT networks, and the perception that these organizations are more likely to comply with ransom demands. Geographically, the United States continues to be a focal point, accounting for nearly half of ransomware incidents in 2024, as evidenced by leak site data.
Global workforce insights: resource strain, mid-career entrants, and demand for soft skills
Assessing the global cybersecurity workforce, a survey of over 15,000 practitioners and decision-makers reveals ongoing challenges with resource reductions, with 25% reporting layoffs and 37% facing budget cuts. As a result, 67% of respondents indicated they lack sufficient staff to meet their objectives.
Hiring managers identified cloud computing security as the most sought-after technical skill (36%), followed by security engineering, risk assessments, and application security (25-28%). However, non-technical skills such as problem-solving, teamwork, collaboration, curiosity, and communication were prioritized over technical expertise by hiring managers, reflecting a preference for adaptable, transferable skills as AI is theorised to increasingly supplement specific technical roles.
Interestingly, the data shows that new entrants to the cybersecurity workforce are trending older, with 35% aged 39-49 and 30% aged 30-38. This suggests that many professionals are transitioning to cybersecurity mid-career, often from fields like software engineering.
Passwords used less as passkeys gain popularity
A survey of over 10,000 people shows a significant decline in password usage among customers in the two years since passkeys were introduced. Designed to reduce phishing risks and enhance user experience, a passkey—a secret key stored on a user’s device—enables users to sign into services using the same method they use to unlock their device (e.g., biometrics, PIN, or pattern). The survey also indicates that 28% of consumers prefer biometrics over other authentication methods, likely due to the convenience of automatic facial recognition.
Data breaches caused by unmanaged API sprawl
The proliferation of digital services has driven a surge in the number of APIs organizations use, with one study revealing that over half manage at least 500 interfaces. Additionally, 57% reported experiencing at least one data breach due to APIs in the past two years. Highlighting challenges with visibility and control, the study urges organizations to mitigate API risk by creating an inventory and prioritizing endpoints that handle sensitive data.
Reports monitored: 29 October - 4 November 2024
To take a deeper dive in the topics most relevant for you, we've listed all the research reports that were published during the observed period.
About
evisec's Cybersecurity Research Digest provides security leaders verified strategic insights via a carefully curated weekly summary of evidence-led, unbiased and objective cybersecurity research publications. Read more about our service here.
✉️ Suggestions or want to collaborate? Get in touch via LinkedIn or email (henry@evisec.xyz)




