CRD #11
On managing outages, framing GenAI risks, zero-day use, security tooling, and SaaS and API observabilty.

The Cybersecurity Research Digest cuts through the marketing fluff and bias to bring you relevant and objective insights, all backed by empirical data.
The post features highlights from trustworthy research sources released between 5 and 18 November 2024, followed by a list of all monitored reports.
Five Eyes agencies: more zero-day exploitation observed
The Five Eyes alliance cybersecurity agencies (US, Australia, Canada, New Zealand, UK) released a co-authored advisory on the most routinely and frequently exploited CVEs by malicious actors in 2023. While the report provides detailed information and ranking on specific vulnerabilities, the advisory emphasizes a notable shift: unlike previous years, when older, unpatched vulnerabilities were most commonly targeted, 2023 saw a significant rise in zero-day exploits.
According to the advisory, the most exploited vulnerabilities were found in networking devices (Cisco), remote access servers (Citrix), and firewalls (Fortinet), highlighting a trend where attackers increasingly focus on widely used technologies to cause widespread and sustained damage across thousands of organizations.
Better framing needed to address GenAI risks
A survey of over 500 security professionals reveals that, while GenAI is perceived as the top priority for security specialists, associated risk assessments often lack clarity, making them difficult to operationalize. The survey highlights a wide range of concerns with the technology, all deemed relatively equal in importance, with no single issue taking precedence. These concerns included training data leaks, unauthorized AI usage, hallucinations, AI bias, model hacking, prompt injection, and the creation of fake content.
The study highlights a critical issue: treating "GenAI" as a single category to understand risks often overgeneralizes the analysis, rendering it ineffective for addressing specific security challenges. For example, current discourse would benefit from a clear distinction between AI "safety" and "security": AI safety pertaining to mitigating harm caused by the outputs generated by the technology, while AI security focusing on protecting AI applications from malicious manipulation (i.e. safeguarding the confidentiality, integrity, and availability of the systems and data they interact with).
Resilience realities: frequent outages persist, yet responses stay reactive
Based on a survey of over 1,000 senior technology executives worldwide, IT outages are widespread, with nearly 70% reporting service interruptions once or more per week. The average annual revenue loss due to outages was estimated at $222,323 over the past twelve months.
Referring to the CrowdStrike outage as a global wake-up call, leaders express widespread concern as 95% acknowledge operational weaknesses that leave them vulnerable, and 48% believe their organizations aren’t doing enough to enhance resilience. Notably, 39% of executives describe their approach to handling outages as “reactive,” responding only as incidents occur, without formal protocols or response plans. Only a third report having an organized response strategy in place.
Emphasizing the importance of organization-wide operational resilience, the study underscores that cybersecurity is just one of many contributors to outages. Non-security factors, including network issues, software and hardware failures, third-party disruptions, capacity constraints, and human error, play equally significant roles. To address this complexity, organizations should adopt resilience strategies that are not tied to specific causes — for example, implementing robust backup and restoration processes and regularly conducting incident response and disaster recovery exercises.
More tools and more features, but less security?
A study of over 2,000 security decision-makers across industries reveals a paradox: organizations with fewer tools report fewer incidents. The report attributes this to the absence of systemic secure-by-design approaches among organizations that tend to rely on a piecemeal strategy, deploying multiple tools to address individual threats. The paradox may also reflect differences in security budgets – larger organizations can afford pricey "all-purpose" platforms or high-end managed service providers, while smaller organizations are forced to figure out more cost-effective solutions tailored to their most pressing threats or compliance requirements.
The study reveals that enterprises with 300+ employees use an average of 10 security tools. Unsurprisingly, 62% of decision-makers prefer expanding features on existing tools rather than replacing them. However, the report suggests rethinking this approach, as it may be less effective. Advocating for a reassessment of security stacks, the study highlights that organizations replacing outdated tools instead of expanding their functionality report 20% fewer security incidents annually.
Shadow IT and misconfigurations: the challenge with SaaS apps
A study analyzing third-party software usage across more than 50 organizational environments highlights significant security challenges associated with SaaS applications in enterprises. On average, the organizations were using close to 500 SaaS applications, with over half unauthorized and operating outside the oversight of security teams — underscoring the persistent issue of shadow IT and unvetted software.
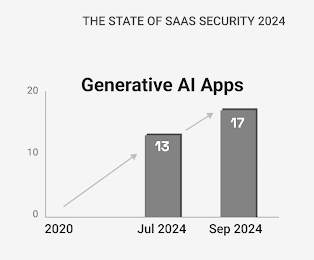
The study also found that organizations now use an average of 17 GenAI applications, up from 13 in July — a 30% increase in just one quarter. Security teams are struggling to manage this rapid growth, as the report identified numerous SaaS instances, including platforms like Snowflake and Salesforce, misconfigured in ways that allowed unauthorized access to sensitive data.
API security: rising incidents and gaps in observability
A survey of over 1,000 security leaders and practitioners highlights the ongoing challenges with API security, with 84% reporting at least one API-related security incident in the past 12 months — marking a steady rise from 2022 and 2023.
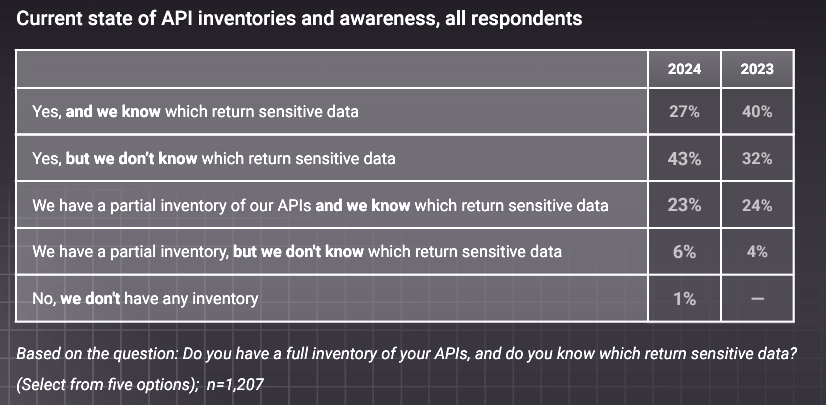
The report advocates for regular testing and enhanced observability, emphasizing that organizations struggle with low visibility into critical API dependencies. Among those with complete API inventories — a significant achievement in itself — only 27% know which APIs handle sensitive data, underscoring the need for improved oversight and management.
Reports monitored: 5-18 November 2024
To take a deeper dive in the topics most relevant for you, we've listed all the research reports that were published during the observed period.
About
evisec's Cybersecurity Research Digest provides security leaders verified strategic insights via a carefully curated weekly summary of evidence-led, unbiased and objective cybersecurity research publications. Read more about our service here.
✉️ Suggestions or want to collaborate? Get in touch via LinkedIn or email (henry@evisec.xyz)




