CRD #12
On AI-generated code, tool overload, security vs development, managed services uptake, incident costs, initial access methods & more,

The Cybersecurity Research Digest cuts through the marketing fluff and bias to bring you relevant and objective insights, all backed by empirical data.
The post features highlights from trustworthy research sources released between 19 and 25 November 2024, followed by a list of all monitored reports.
Cloud security challenges: tool overload, DevOps vs SecOps conflict, AI-generated code
A global survey of over 2,800 security leaders and practitioners provided unique insights on key challenges in cloud security. First, the sheer number of solutions in use is creating significant security blind spots. On average, organizations rely on 12 cloud service providers and 16 cloud security tools, leading 98% of respondents to stress the need for consolidation and simplification to improve visibility and management.
Second, conflict between DevOps and SecOps teams is perceived as a significant issue, with over half of respondents identifying security as the primary gating factor delaying software releases. In fact, 84% report that security processes are the main source of delays, yet 71% acknowledge that rushed time-to-market pressures still result in security vulnerabilities.
Third, somewhat surprisingly, AI-generated code was ranked as the top security concern, surpassing more standard worries related to APIs, access management, insider threats, or unmanaged assets. This prioritization reflects the undeniable reliance on GenAI, with 100% of respondents reporting the adoption of AI-assisted application development.
Managed services on the rise amid talent shortages and tooling inefficiencies
A global survey of 1,484 IT decision-makers in companies with 250+ employees estimates that the average direct revenue loss from cyberattacks last year was 9%. With a persistent shortage of skilled talent remaining a top concern, organizations are adopting varied strategies to address the gap. Nearly half plan to increase spending to attract the right talent, while close to a fifth are reducing hiring budgets, reflecting a growing reliance on Managed Security Services. This area has become a priority for many businesses, with 50% already investing in managed services and an additional 40% planning to do so within the next two years.
The report also examines security stack efficiencies, noting that many organizations are not maximizing functionalities of their security tools, with 45% of tools not being fully deployed. Additionally, referring to hype-led buying decisions, 41% of respondents acknowledge overlapping functionalities among the tools in use, leading to continued overspending. False alerts remain a key challenge in the industry, with an estimated 34% of alerts deemed false positives — an improvement from 38% reported last year but still indicative of major inefficiencies.
Australian annual threat report: small businesses disproportionately vulnerable
To balance the primarily survey-based data in industry reports, the Australian Cyber Security Centre's annual Cyber Threat Report for 2023-24 offers valuable insights grounded in actual incident response activities and official reports.
The centre reports that the average loss per cybercrime incident rose slightly for small businesses (+8%) to $48,615, while medium-sized businesses saw a significant decrease (-35%) to $62,870, and large businesses experienced a decline (-11%) to $62,602. Despite the overall 8% decrease in costs, the data underscores a persistent challenge: small businesses, which make up the majority of the economy but often lack resources for robust security measures, remain disproportionately vulnerable.
On a positive note, the agency received 7% fewer cybercrime reports compared to the previous year. Most incidents involved email compromise or banking fraud, while ransomware accounted for 11% of incidents, reflecting a 3% increase from last year.
A fourth of ransomware claims linked to VPN as actors diversify
Referring to outdated software and VPN gateways with default or weakly protected credentials, latest insurance data reveals a significant rise in attackers leveraging VPNs for initial access, accounting for a substantial 28.7% of ransomware claims in 2024 Q3.
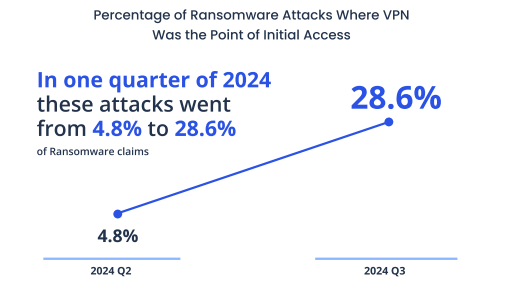
The insurer also highlights a trend corroborated by other threat intelligence providers: law enforcement activities have disrupted the operations of dominant actors like LockBit, leading to a more fragmented ransomware ecosystem. This diversification, however, has not reduced the overall number of successful attacks, as victim numbers remain consistent quarter over quarter. Organizations now face a broader range of tactics, techniques, and procedures employed by an increasingly varied set of threat actors.
Predictable yet unresolved: striking when defences are weakest
A survey of 900 IT and security professionals confirms a well-known reality for those experienced in cyber incident response: hackers strike when organizations are most vulnerable. According to the survey, 72% of respondents reported being attacked on a holiday or weekend, and 63% experienced ransomware attacks during corporate events like mergers, acquisitions, or IPOs.
Despite this awareness, the report reveals that 85% of organizations with 24/7 SOC capabilities reduce staffing by up to 50% during holidays and weekends. The reasons are clear — overtime costs can be difficult to justify to clients, and staffing challenges persist as employees are often unwilling to forgo precious personal time.
Identity scammers embracing GenAI: deepfakes and digital document forgeries dominate
Data from tens of millions of identity verifications in 2024 reveals that deepfakes — digitally manipulated photos or videos — have become the primary technique for bypassing online identity verification processes. Occurring at a rate of one every five minutes according to the company's telemetry, deepfakes were used in 40% of biometric fraud attempts.
Highlighting further use of GenAI by fraudsters, the study reports a 244% year-over-year increase in digital document forgeries, which have now overtaken physical counterfeits as the dominant method of document fraud. The report also reveals that identity fraud primarily targets financial industries, with crypto-related platforms leading the list, followed by lending services and traditional banks.
Reports monitored: 19-25 November 2024
To take a deeper dive in the topics most relevant for you, we've listed all the monitored research reports (26) that were published during the observed period.
About
evisec's Cybersecurity Research Digest provides security leaders verified strategic insights via a carefully curated weekly summary of evidence-led, unbiased and objective cybersecurity research publications. Read more about our service here.
✉️ Suggestions or want to collaborate? Get in touch via LinkedIn or email (henry@evisec.xyz)




