CRD #14
On human risk stats, artifacts vs LOLbins, security-specific GenAI & more.

The Cybersecurity Research Digest cuts through the marketing fluff and bias to bring you relevant and objective insights on cybersecurity stats and trends, all backed by empirical data.
The post features highlights from trustworthy research sources released between 10 and 22 December 2024, followed by a list of all monitored reports.
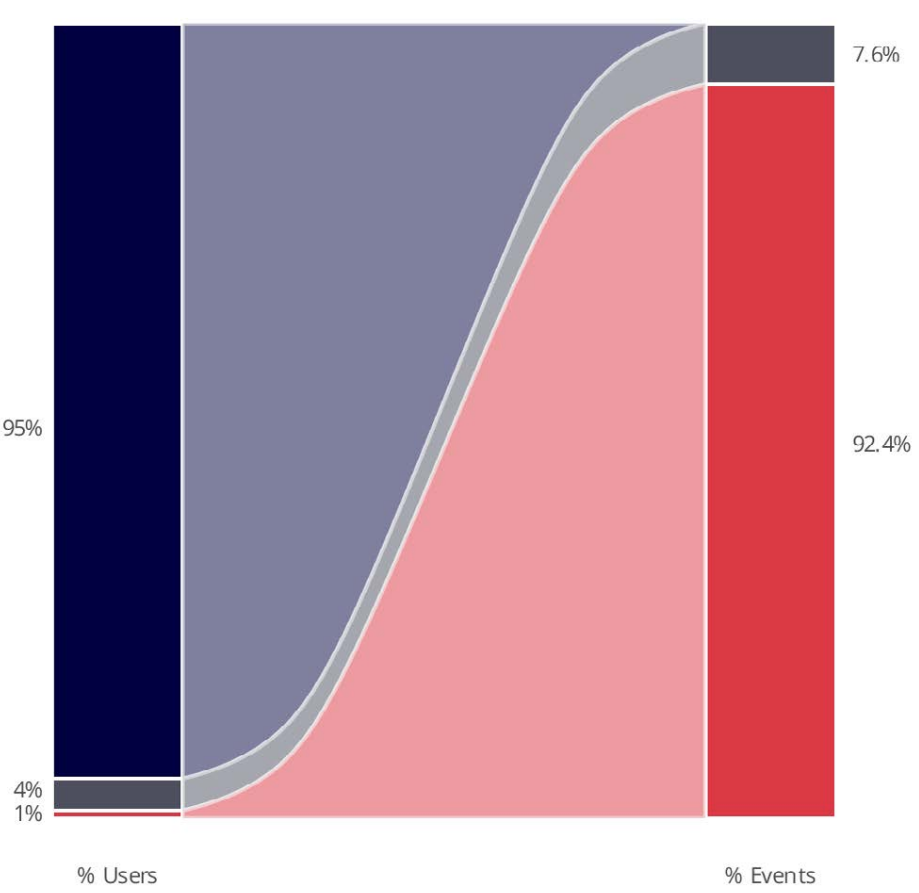
Understanding human risk: the 1% driving most security events
Analysis of human risk behaviors shows that a small number of users are responsible for a disproportionately large share of risky activity. In the most extreme example, the research reveals that 1% of users are behind 92% of all malware events. While concerning, this finding offers actionable insights for security teams to create more effective programs by implementing risk-specific, role-based protections and training.
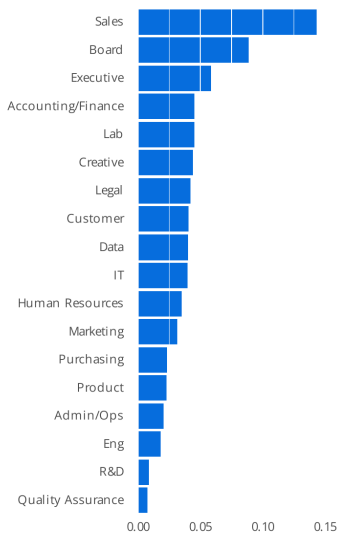
The study also highlights the types of targets most often end up falling for social engineering attacks. These tend to be managerial roles—especially in sales, board, executive, and finance teams—rather than employees or contractors. This does not reflect the cybersecurity capacity of individuals in these roles but rather their increased exposure as public-facing figures, making them frequent targets.
Shift in attacker strategies: LOLbins on the rise
Incident response and MDR data highlight a growing need for organizations to strengthen their detection and defense strategies against the misuse of legitimate tools.
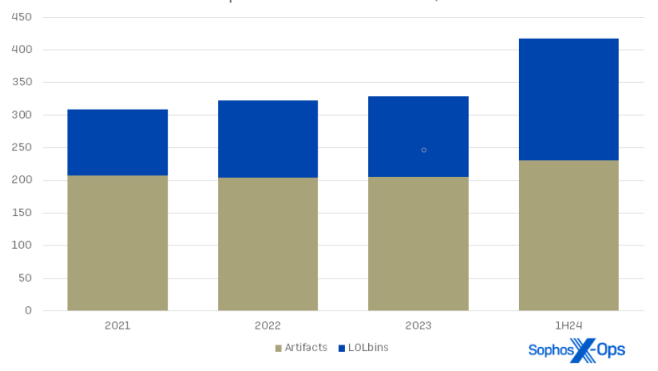
Threat actors are increasingly exploiting unique LOLbins—legitimate software binaries used for malicious purposes. Unlike "artifacts," such as Mimikatz or Cobalt Strike, which are illicit third-party tools, LOLbins allow attackers to camouflage their activities within legitimate system processes. The analysis shows that RDP, cmd.exe, and PowerShell remain the most frequently abused LOLbins.
Security-specific GenAI: interest high, but most still evaluating
A survey of 1,000 security professionals reveals strong interest in security-specific GenAI, though adoption remains limited. Only 6% of respondents have purchased GenAI solutions, with another 11% in the process of buying. The majority of security teams are still considering adoption, with 32% exploring the technology, 29% actively searching, and 18% testing or evaluating tools.
Notably, 63% of respondents indicated they "would change security vendors to use the GenAI of another vendor." Given the strong retention typically seen in security products, this creates a unique opportunity for vendors to challenge incumbents.
However, the study also underscores that calculating ROI is the top economic concern for potential adopters. Thus, to succeed, GenAI tools must go beyond the LLM hype and demonstrate measurable value over existing solutions.
Cyber insurance uptake grows, but confidence in coverage declines
A survey of over 500 North American companies with, or considering, cyber insurance reveals that more organizations than ever are purchasing coverage, with most choosing standalone policies rather than expanding existing general insurance packages.
This rise in adoption—driven by regulatory requirements and greater awareness of related risk mitigation benefits—has, however, been accompanied by significantly reduced confidence in the adequacy of coverage. These concerns likely relate to whether policies effectively address risks posed by highly advanced cyber operations, including those linked to nation-states/APTs.
At the same time, the steep premium rate increases of recent years have slowed, with insurers now projecting average hikes of 10% or less.
HR professionals battling fraud in recruitment
Fraudulent job applications have become a significant challenge for HR professionals, with 44% encountering such cases. Alarmingly, a third of these applications contained cybersecurity threats, such as malicious links or attachments—highlighting the need to address this vector as a priority within security programs.
Moreover, not all instances of fraud are detected during the initial stages of recruitment. In fact, 40% of professionals admit that fraudulent applications were only uncovered after the candidates had progressed further in the hiring process.
OT security: legacy systems, low visibility, and questioning security tools
A global study of more than 400 industrial control system (ICS) practitioners highlights ongoing challenges in securing OT and IoT environments. On average, over 40% of OT/IoT assets are categorized as legacy, outdated, or end-of-life. These findings correlate with significant visibility gaps, with respondents estimating that more than 38% of their OT/IoT network is not visible—an issue that is even more pronounced in critical operational networks.
However, poor visibility and outdated devices do not necessarily automatically lead to increased cyber risks – for example, study also reveals that practitioners sometimes view improperly implemented security tools as more disruptive to production environments than actual cyberattacks.
Reports monitored: 10-22 December 2024
To take a deeper dive in the topics most relevant for you, we've listed all the monitored research reports (26) that were published during the observed period.
About
evisec's Cybersecurity Research Digest provides security leaders verified strategic insights via a carefully curated weekly summary of evidence-led, unbiased and objective cybersecurity research publications. Read more about our service here.
✉️ Suggestions or want to collaborate? Get in touch via LinkedIn or email (henry@evisec.xyz)




