CRD #16
On CISO executive influence, security tool sprawl, the Pareto Principle, DDoS trends and more.

The Cybersecurity Research Digest cuts through the marketing fluff and bias to bring you relevant and objective insights on cybersecurity stats and trends, all backed by empirical data.
The post features highlights from trustworthy research sources released between January 21–February 2, 2025, followed by a list of all monitored reports.
Mixed indicators on CISOs and executive influence
A recent survey, which included 600 respondents (500 CISOs, CSOs, or equivalent security leaders and 100 board members), reports a very significant increase in the number of CISOs reporting directly to the CEO: in 2023, this figure was 47%, but it nearly doubled to 82% in 2024. However, other studies as well as feedback from the industry indicate that the actual number of CISOs directly reporting to the CEO may be significantly lower — some 2023 studies place this figure at 20%, while others suggest it could be as low as 5%.
These discrepancies highlight the challenge of interpreting such statistics, as methodologies and respondent demographics vary across vendor reports. In this case, larger organizations in highly regulated industries may be more likely to integrate CISOs into executive leadership — these types of factors are often either not highlighted or explained. Thus, such survey data should be viewed as broad trend indicators, and decision-makers and analysts relying on such insights should always compare findings across multiple studies before drawing conclusions.
The same survey also drew attention to the ethical dilemmas CISOs face, with 21% of respondents revealing they had been pressured not to report a compliance issue. Additionally, 59% claimed they would become whistleblowers if their organization ignored compliance requirements — this once more seems quite high and self-reported data on such questions may not always reflect real-world actions. Whatever the real numbers, these again serve as telling indications of significant issues security leaders face.
Average organization: 83 security solutions from 29 vendors
A study advocating for increased security platformization claims that the average organization operates 83 different security solutions from 29 vendors. While the respondent demographics are unclear, these figures suggest that the study likely focused on large enterprises.
According to the survey, 52% of executives cite complexity as the primary impediment to security operations. The report further claims that organizations embracing platformization achieve an average ROI of 101%, compared to just 28% among those that do not consolidate their tools.
While the report supports an obvious business agenda, it is difficult to argue against the benefits and attractiveness of consolidation for security leaders, particularly given the operational inefficiencies associated with managing dozens of disparate security solutions.
On the effectiveness of "basic" security measures
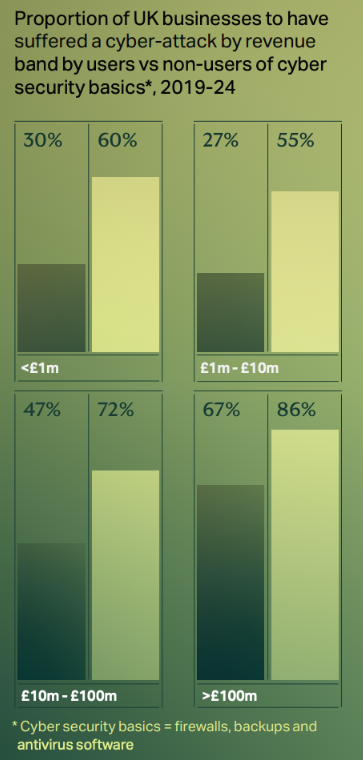
A UK-based survey of 900 IT decision-makers points out that organizations that have widely implemented basic cybersecurity measures — defined very broadly as firewalls, endpoint protection, and antivirus software — experience a 75% reduction in cyber incident costs.
While this claim is based on limited survey data and broad definitions, it reinforces the Pareto Principle: simply put, a relatively small investment in foundational security measures can prevent the majority of incidents.
Threat actors and GenAI: no breakthrough (yet!)
Google’s recent report, informed by observations of its LLM, Gemini, assesses how threat actors have thus far attempted to leverage GenAI to carry out cyber operations. The findings indicate that adversaries remain in an experimental phase, primarily using GenAI for research, troubleshooting code, and content creation rather than developing genuinely novel offensive techniques.
The report also notes that state actors (APTs) have likely leveraged Gemini across multiple attack phases, including reconnaissance, vulnerability research, payload development, and scripting assistance. Here, Iranian APT groups appeared to be the most active users, while Russian APT activity was seen as minimal (at least for Gemini use).
Despite efficiency and scalability gains for both experienced and less skilled attackers, the assessment by Google remains that GenAI has not yet introduced breakthrough offensive capabilities. However, its clear that as AI models and agentic systems are released to the public with little consideration of their implications for offensive capabilities, the cybersecurity landscape may shift rapidly, necessitating continuous monitoring of related threat actor activity.
DDoS attack trends: short bursts, diverse methods, and rising extortion
A recent analysis of Q4 2024 DDoS attack data shows that DDoS attacks are typically short bursts, with 72% of HTTP DDoS incidents lasting under ten minutes. However, approximately 22% extend beyond an hour, and 11% persist for more than 24 hours.
The data also shows that Layer 3/Layer 4 and HTTP-based attacks occur in nearly equal proportions. Among Layer 3/Layer 4 attacks, SYN flood was the most common vector, accounting for 38% of attacks, followed by DNS flood attacks at 16% and UDP floods at 14%. For HTTP-based attacks, the GET method was used in nearly 70% of malicious requests, followed by the POST method at 27%.
High-confidence attribution of DDoS attacks remains very difficult, but among those able to identify likely threat actors, 40% of respondents pointed to competitors, while 17% suspected state-sponsored actors, a similar percentage cited disgruntled users or customers, and 14% attributed attacks to extortionists. Notably, ransomware groups increasingly leverage DDoS as an extortion tool, with a 78% quarter-over-quarter increase and 25% year-over-year growth in ransomware-linked DDoS activity.
Ransomware in 2024: more groups, faster attacks, and deeper specialization
Research from Rapid7 identified over 75 active ransomware groups in 2024, underscoring a low barrier to entry that enables new actors to emerge. However, established groups such as RansomHub, Akira, and Fog appear to have strengthened their positions through sophisticated extortion tactics and expanded affiliate networks. Double and triple extortion tactics are now considered standard practice, with attackers demanding payments for decryption, data suppression, and protection against further attacks, including DDoS threats.
At the same time, another analysis indicates that threat actors in 2024 demonstrated faster breakout times, defined as the time from initial access to lateral movement. The average breakout time dropped to 48 minutes, a 22% improvement in speed compared to 2023. Additionally, ransomware-as-a-service (RaaS) groups showed increased specialization, dividing attacks into distinct phases handled by different affiliates, mirroring an assembly-line approach.
Furthermore, a review of 2024 vulnerability exploitation trends shows a 20% increase in exploited CVEs compared to 2023, when 639 CVEs were publicly reported as exploited in the wild. Overall, just 1% of published CVEs were confirmed as exploited in the wild, consistent with previous years.
Reports monitored: 21 January - 3 February 2025
To take a deeper dive in the topics most relevant for you, find below a list of all the monitored research reports (28) that were published during the observed period.
About
evisec's Cybersecurity Research Digest provides security leaders verified strategic insights via a carefully curated weekly summary of evidence-led, unbiased and objective cybersecurity research publications. Read more about our service here.
✉️ Suggestions or want to collaborate? Get in touch via LinkedIn or email (henry@evisec.xyz)




