CRD #21
On cyber-enabled crime stats by FBI, trends in access vectors, dwell times, ransomware, security budgets, and more.

The Cybersecurity Research Digest cuts through the marketing fluff and bias to bring you relevant and objective insights on cybersecurity stats and trends, all backed by empirical data.
This post features highlights from trustworthy research sources released between April 15 and 29, 2025, followed by a list of all monitored reports.
TL;DR
- Cyber-enabled crime continues to grow: FBI reports record losses of $16.6B in 2024 (up from $12.5B in 2023), with fraud as the leading contributor.
- Ransomware remains dominant: 9% YoY rise in critical infrastructure complaints; 37% YoY increase in ransomware-related breaches.
- Initial attack vectors shifting slightly: phishing declines, while credential abuse and brute-force attacks rise.
- SMBs hit hardest: ransomware involved in 88% of breaches for SMBs vs. 39% for large organizations.
- BYOD and shadow IT risks: nearly half of credential exposures stem from unmanaged devices.
- Detection remains weak: 96% of breaches discovered via disclosures by threat actors.
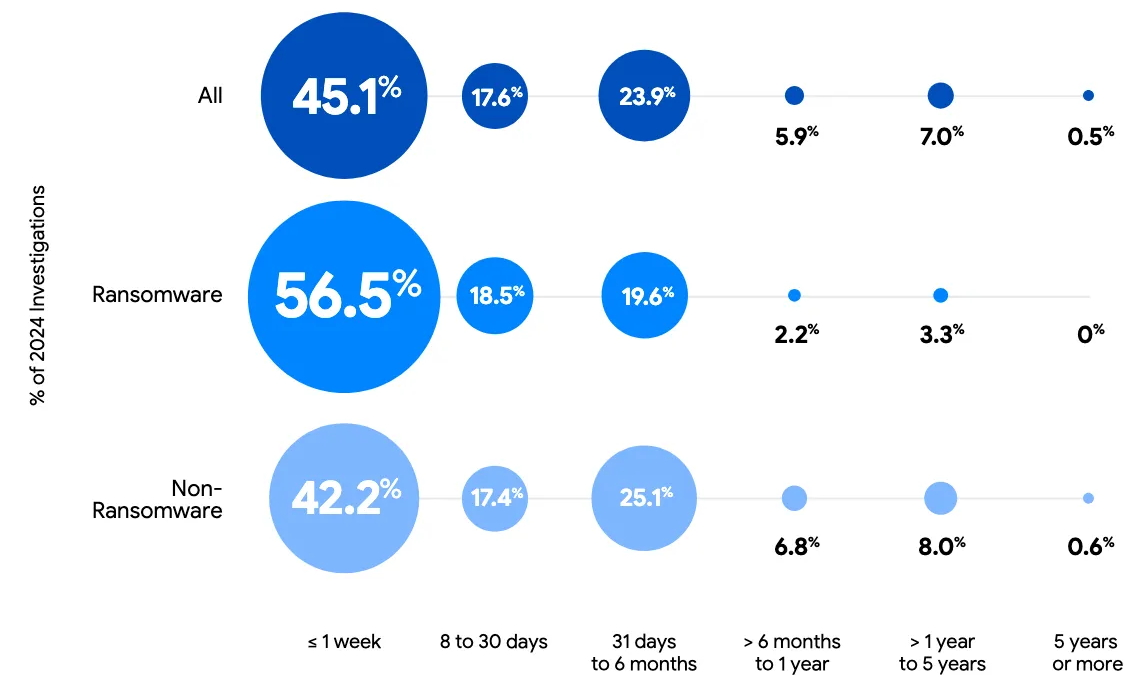
- Dwell times: median breach dwell time stabilizes around 10–11 days; ransomware actors are moving faster.
- Cyber budgets remain resilient: 80% expect increases, especially mid-sized firms; vendor consolidation still limited.
- Stock market impact: Cyber incidents linked to sustained stock price drops, though evidence is mixed. A dedicated evisec special report on the topic is planned for later this year.
As cybersecurity vendors ramped up their analytical content for RSA, the past few weeks have seen an exceptional volume of new research. This includes the release of several flagship reports that have shaped industry understanding over decades already: Verizon’s Data Breach Investigations Report (DBIR, since 2008), Google’s M-Trends (formerly by Mandiant, since 2010), and the FBI’s annual Internet Crime Report (since 2001). These long-running reports stand apart from the many newer and similar reports that emerge each year, offering consistently high-quality analysis and a global snapshot of cybersecurity trends, rooted in unique datasets.
This CRD covers the main highlights from these cornerstone reports, alongside other recent publications that stood out. For a deeper dive, an organized list of all reports is available at the end of this issue to help you navigate the topics most relevant to you.
Cyber-enabled crime stats: losses continue to grow steadily
Based on statistics reported to the FBI’s Internet Crime Complaint Center (IC3), 2024 marked yet another record for reported losses from cyber-enabled crime, $16.6 billion—a significant increase from $12.5 billion in 2023. The FBI data encompasses all cyber-enabled crime, not just cyber breaches, with the bulk of reported losses stemming from various types of fraud.
While the rising numbers likely also reflect higher reporting rates, the trend is clear: internet-related crime is steadily growing, in line with our increasing dependence on digital technologies. The FBI highlights the scale of this evolution: in its early years, IC3 received about 2,000 complaints per month; for the past five years, it has averaged over 2,000 complaints per day.
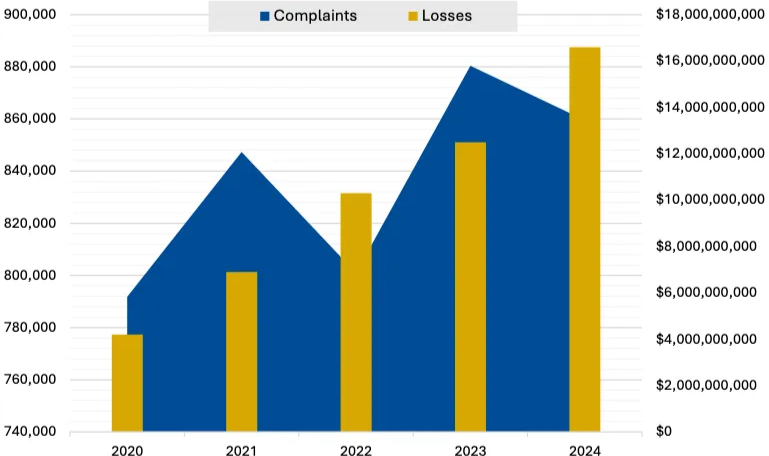
In terms of cybersecurity-specific activity (i.e., affecting the confidentiality, integrity, or availability of data), ransomware remains the dominant threat to critical infrastructure, as complaints rose 9% from 2023, with manufacturing, healthcare, government, and financial services being the most targeted domains.
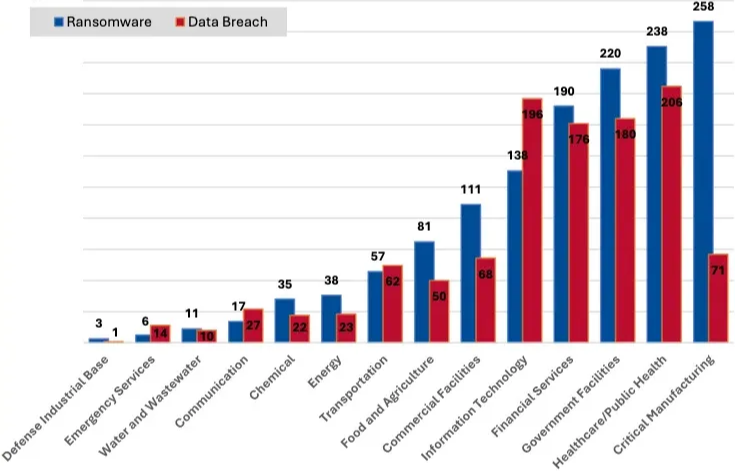
Main ways in: vulnerability exploitation and stolen credentials
Both the DBIR and M-Trends reports tell a similar story: threat actors exploit technical vulnerabilities and human weaknesses alike, and both require equal attention in defensive strategies. Whilst most indicators of initial attack vectors have remained relatively consistent according to the M-Trends reports — with exploits continuing to lead — the analysis highlights that email phishing has declined, while stolen credentials, likely obtained via infostealers rather than social engineering, have become more prominent.
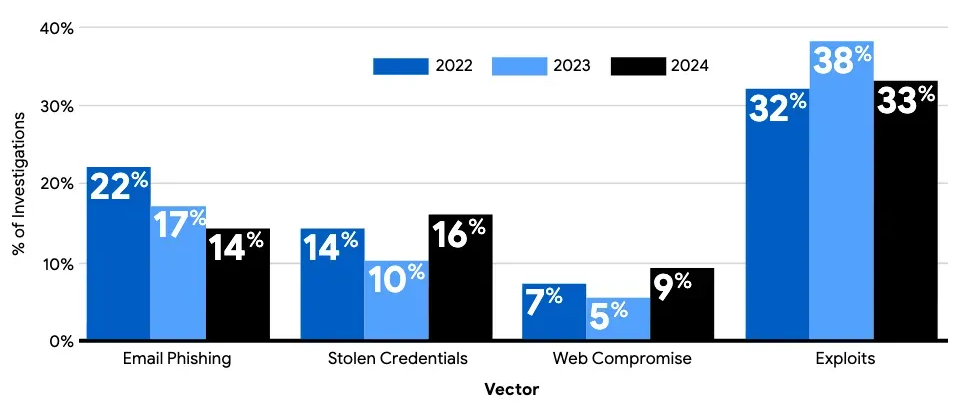
In contrast, for ransomware-specific incidents, brute-force attacks (e.g., password spraying, default VPN credentials, and high-volume RDP login attempts) dominate as the initial infection vector, reinforcing the importance of basic controls such as MFA and account lockout policies.

The DBIR reports that ransomware — whether encryption-based or not — saw a 37% year-over-year increase and was present in 44% of all breaches examined (up from 32%). At the same time, the median ransom payment dropped from $150,000 to $114,000. This shift may be linked to increased targeting of smaller businesses: ransomware was present in 39% of breaches affecting large organizations, compared to 88% (!) for SMBs.
Nevertheless, to balance the emphasis on "technical" initial access methods, broader human vulnerabilities remain just as relevant — if not more so. DBIR's data underscores this, with credential abuse (which often involves social engineering) and phishing ranking among the top initial access vectors, alongside numerous breaches resulting simply from human error or misuse.
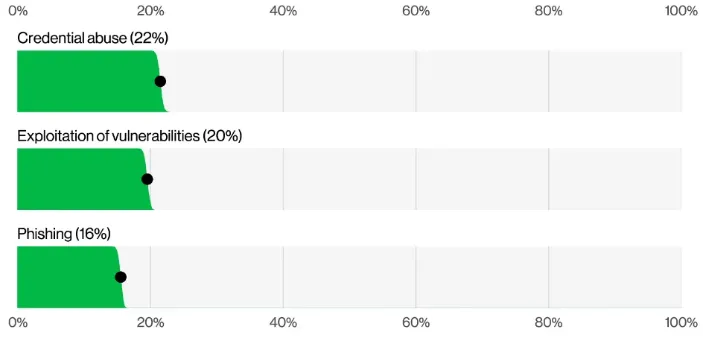
With regard to infostealers and credential abuse, the DBIR notes that 30% of known compromised systems were identified as enterprise-licensed devices. Among those with corporate logins in exposed credential data, however, 46% were non-managed and contained both personal and business credentials. A similar pattern emerges in the context of GenAI platform use: 72% of authentication to these services came via non-corporate accounts. These dynamics likely reflect issues with both BYOD and personal account usage oversight, as well as enterprise-owned devices operating outside approved policy.
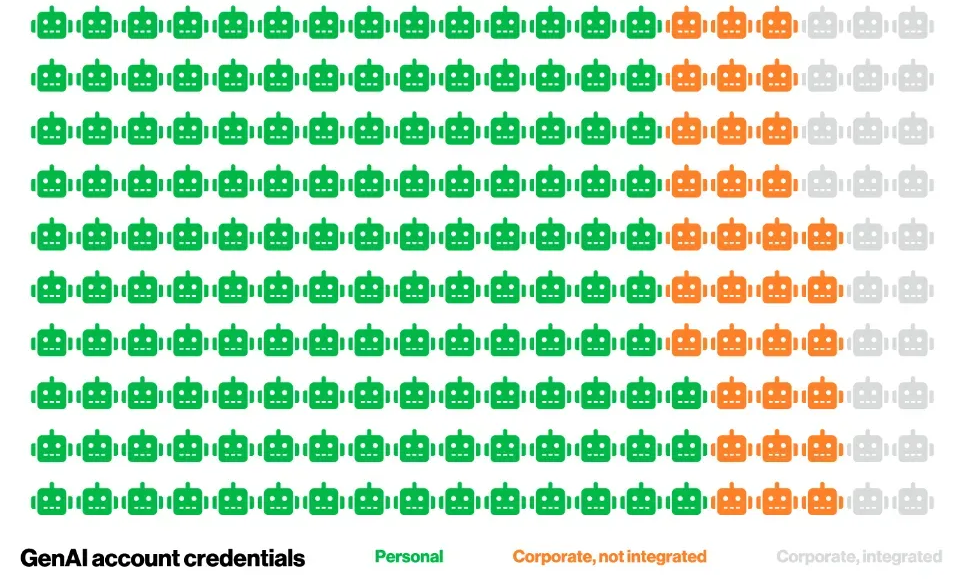
"Assume access, ready defenses": on detection inefficiencies and shortening dwell times
The M-Trends report highlights that in 2024, 57% of organizations learned of a compromise through external sources (i.e. not internal detection or employee reporting).
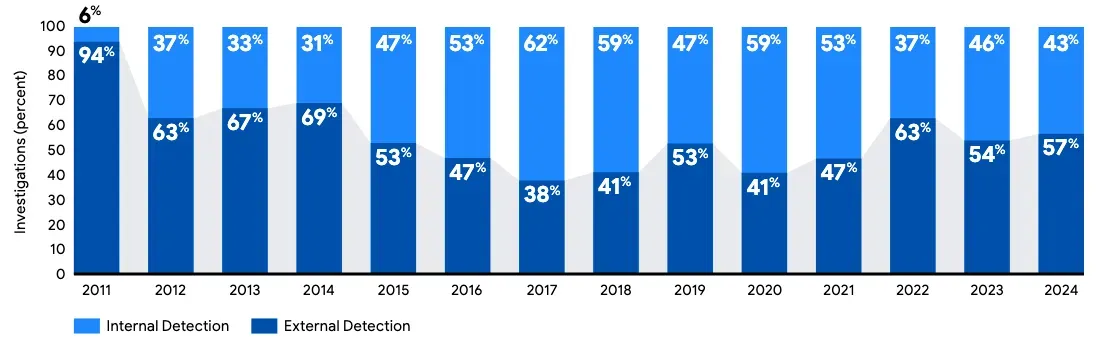
The DBIR shows an even starker figure: 96% of breaches were discovered externally — through notifications from threat actors — while only 4% were detected through internal technical means:
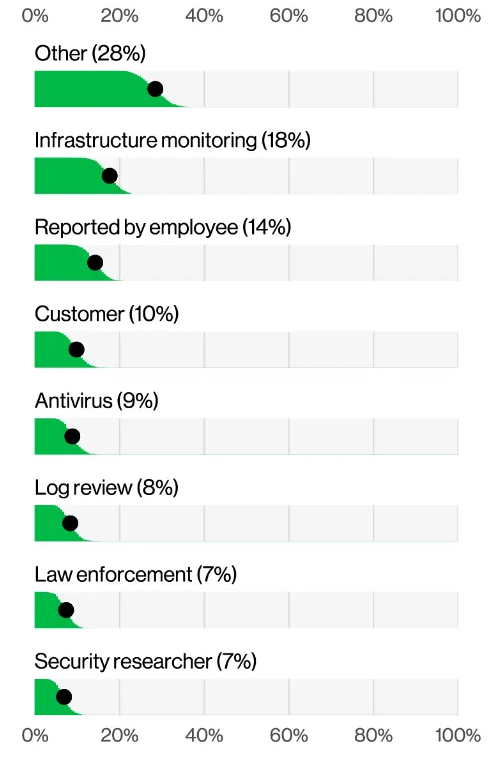
The data tells a simple story: once attackers are in, they will likely not be stopped in time, and will achieve their malicious goals. This reinforces the relevance of the "assume breach" mindset, which prioritizes building strong reactive capabilities to strengthen resilience — rather than focusing solely on the often unrealistic goal of prevention and timely detection. The DBIR proposes a better slogan with "assume access, ready defenses."
On dwell times — the number of days an attacker remains undetected — the global median has continued to decrease, though signs now point to the metric stabilizing around 10–11 days.
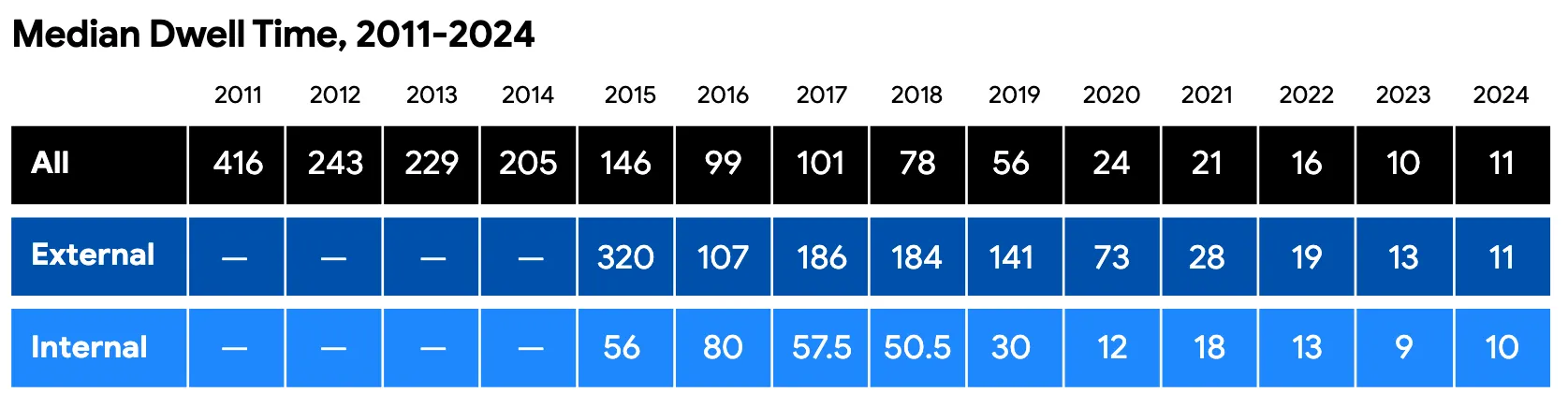
However, ransomware-related intrusions show a noticeably different dwell time pattern, with a stronger concentration toward shorter intervals between evidence of initial malicious activity and detection. According to Mandiant, 56.5% of these intrusions in 2024 were discovered within a week.
Cyber budgets hold steady, vendor consolidation stalls
Despite economic and political headwinds, a recent survey shows that cyber budget growth appears stable. Ransomware and supply chain threats continue to drive spending as cloud security and GenAI protection were identified as the top areas of investment.
80% of all respondents expected budget increases (a slight drop from last year’s 87%), with midsize companies planning the most growth: 97% expected budget increases and 36% anticipated double-digit year-on-year growth.
Surprisingly, vendor consolidation remains limited as per the survey, despite other reporting on the trend becoming more prevalent: while 40% plan to expand their vendor mix (down from 51%), 48% foresee no change. Only 9% expect to reduce vendor count, though this figure rises to 16% among Global 2000 organizations. Motivations for vendor changes vary: new threat vectors (32%) and business growth (24%) were top reasons for expansion, while those consolidating cited the need for streamlined oversight and better control. The shift toward platform-based defense models, however, continues, especially in areas like endpoint protection, identity, and network monitoring.
Cyber incidents and stock price impact
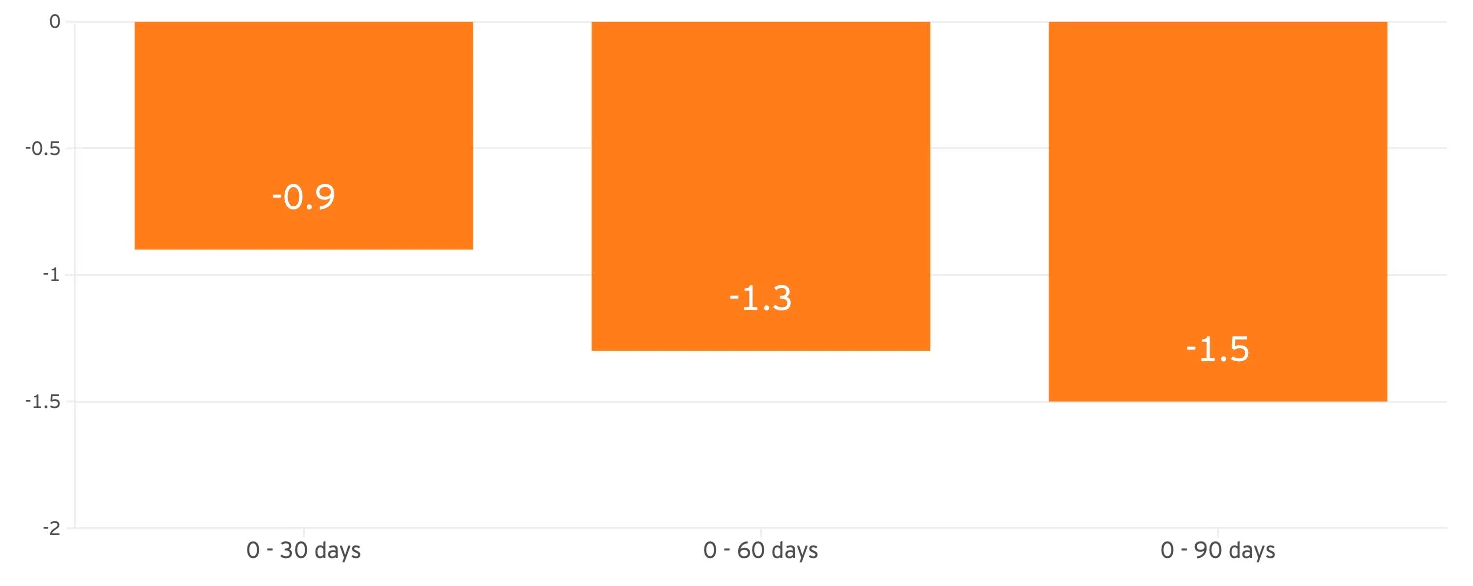
EY reports that cybersecurity incidents correlate with stock price declines, not only immediately post-disclosure but for up to 90 days. This analysis suggests that cyber incidents carry longer-term financial consequences. However, this interpretation should be treated with caution, as other research has found no significant impact from cyber breaches. A deeper dive into this topic is planned in a forthcoming evisec special research report.
Reports monitored: April 14-29
To take a deeper dive in the topics most relevant for you, find below a list of all the monitored research reports (32) that were published during the observed period.
About
evisec's Cybersecurity Research Digest provides security leaders verified strategic insights via a carefully curated weekly summary of evidence-led, unbiased and objective cybersecurity research publications. Read more about our service here.
✉️ Suggestions or want to collaborate? Get in touch via LinkedIn or email (henry@evisec.xyz)




