CRD #23

The Cybersecurity Research Digest cuts through the marketing fluff and bias to bring you relevant and objective insights on cybersecurity stats and trends, all backed by empirical data.
This post features highlights from trustworthy research sources released between May 20 and June 30, 2025, followed by a list of all monitored reports.
TL;DR
- SOC struggles persist despite reported efficiency gains from AI, with tool sprawl and data silos still widespread
- CVE volumes surged in 2024, with a 61% overall increase and major spikes in Linux and macOS vulns
- Living-off-the-land techniques dominate intrusions, with 84% of attacks leveraging built-in admin tools
- Corporate-targeted fraud increased by 26%, driven by phishing, account takeover, and deepfake-enabled scams
- Hiring managers prioritize general IT knowledge, teamwork and problem-solving over technical cybersecurity skills
SOC challenges persist — is AI making a difference?
Studies reviewed by CRD this year often come with a recurring theme: constant struggles inside most security operations centers (SOCs). The keywords are tool sprawl, alert fatigue, poor data integration, and the resulting human toll — leading to burnout and high staff turnover.
Splunk’s latest survey of over 2,000 security professionals confirms this picture. Nearly half (46%) of respondents say they now spend more time maintaining tools than actually defending against threats. Additionally, data accessibility remains a key issue, with 78% reporting their security tools are dispersed and disconnected, highlighting the longstanding challenge of siloed architectures.
As expected, AI is perceived as the solution. According to the report, 59% already see moderate or significant efficiency gains from using AI. Furthermore, security-specific AI solutions are seen to outperform general-purpose LLMs — 63% of respondents say domain-specific models have significantly or extremely improved their security operations.
While optimism around AI is growing, trust levels still vary. According to the report, 11% of respondents say they fully trust AI in security operations, and 61% express partial trust — notably high figures given the typically risk-averse nature of security teams.
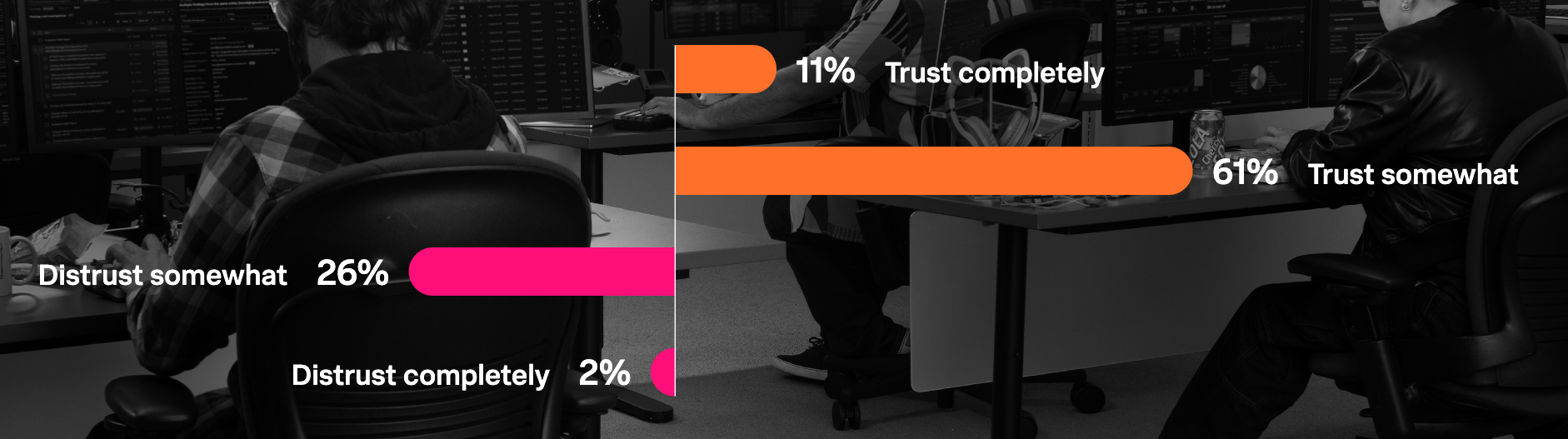
Trust likely depends on how security teams define “AI” — and definitions remain vague. "Truly" agentic AI, where models act and make critical operational decisions autonomously without human oversight, still appears largely aspirational. Furthermore, as the initial hype subsides, it would not be surprising to see reports that AI-based solutions often add complexity rather than clarity in practice, becoming another system to integrate, monitor, and manage.
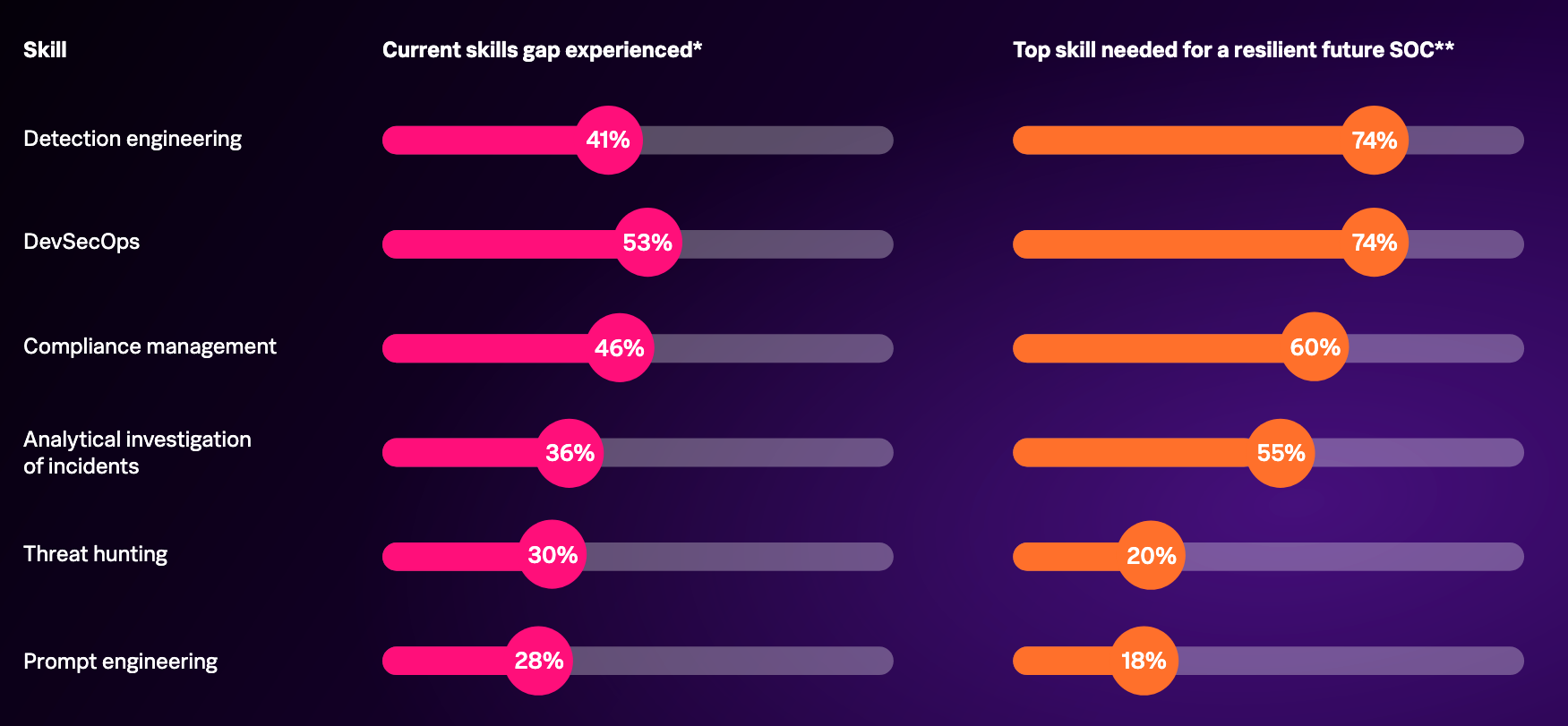
The underlying problems — overworked teams, fragmented data, and persistent skills shortages — haven't gone away so far. It is also telling that, even as AI adoption rises, the perceived core skills needed for the future SOC remain largely the same.
CVEs in 2024: growth in critical flaws; increases re: Linux and macOS
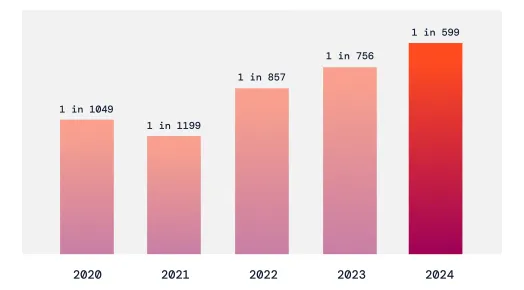
Analysis of 2024 vulnerability data shows that last year brought new records, not just in volume but also in severity. Compared to 2023, the total volume of CVEs grew by 61%, with a significant increase in critical (+37%) and exploited (+96%) vulnerabilities.
Other notable increases in exploitation stats related to user-facing software: Chrome saw an 1840% jump in exploited CVEs, while Microsoft Office followed with +433%. Furthermore, Linux vulnerabilities jumped an unprecedented 967% (3,329 cases), while macOS vulnerabilities increased by 95% year over year (508 cases).
The analysis of last year's CVEs also underscored that attackers increasingly target fewer but higher-impact flaws. Thus, exploitation risk (not just vulnerability count) is the key metric to watch in 2025. In our view, the analysis also signals that operating systems historically perceived as more secure than Windows are now under heightened scrutiny and attack, and must be fully integrated into corporate patching and monitoring practices.
Living-off-the-land techniques dominate modern intrusions
Breaching networks do not necessarily require leveraging software vulnerabilities. New managed detection and response (MDR) telemetry reveals a clear trend: attackers increasingly rely on living-off-the-land (LOTL) techniques that abuse legitimate tools already present in the environment. In a dataset of over 700,000 incidents, 84% of major attacks leveraged LOTL methods — marking a major pivot away from malware-heavy approaches.
Attackers increasingly abuse common admin tools like PowerShell, WMI, RDP, and PsExec — widely used in IT environments — to operate undetected, escalate privileges, and exfiltrate data without deploying traditional malware nor triggering security alerts. This is a growing blind spot in many organizations' threat models — one that demands renewed focus on behavioral detection, context-aware alerting, and reducing unnecessary exposure to high-risk admin utilities.
New realities in corporate-targeted fraud
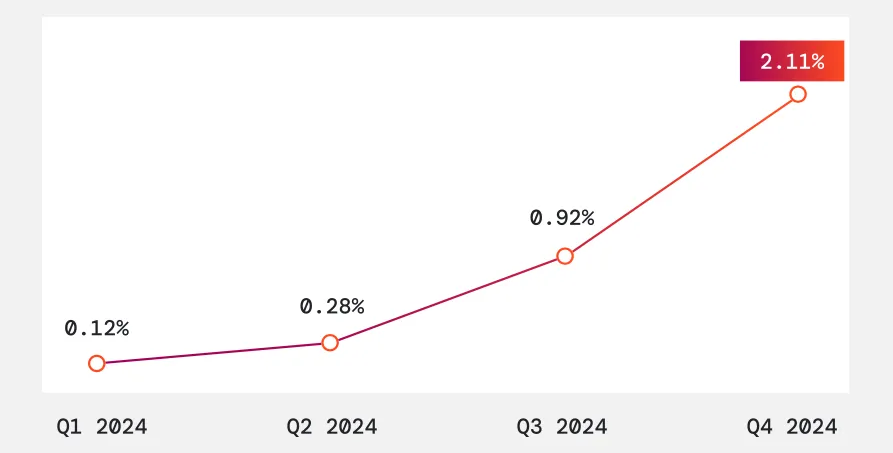
Fraud targeting companies — particularly via call centers — continues to rise, increasingly enabled by low-cost AI tools. According to new data from a major voice authentication firm, enterprise-targeted fraud grew by 26% between 2023 and 2024.
According to the data, most prevalent techniques are:
- Phishing, where attackers elicit sensitive data like login credentials;
- Account takeover, often involving credential resets, fund transfers, or card issuance;
- First-party fraud, in which legitimate users misrepresent themselves for personal gain;
- Account opening fraud, involving fake identities.

Deepfake use in company-targeted fraud calls is also climbing fast, with a marked increase recorded across consecutive quarters through 2024 — signalling a shift toward more sophisticated, AI-enabled deception techniques, and stimulating the market for related detection solutions.
Most security teams to grow; general IT skills and certifications lead hiring criteria
A global survey of 929 security hiring managers highlights both optimism and friction in early-career cybersecurity hiring. While 62% of organizations plan to grow their cybersecurity teams, persistent gaps remain between expectations and candidate readiness.
Certifications and hands-on experience continue to outweigh formal cybersecurity education — 90% of respondents would hire candidates with IT experience alone, and 89% say a certification is often more valuable than a degree (note: this is data from a certification provider).
Internships (55%) and apprenticeships (46%) are regarded as central hiring channels, especially in sectors like government, telecom, and healthcare. There’s also growing openness to recruiting outside the traditional CS/IT talent pool, with a quarter of hiring managers identifying strong candidates from unrelated academic backgrounds.
Despite high concern about reduction of a company's workforce due to employees leaving and not being replaced (58%), most teams report having the budget to both invest in talent development (75%) and expand headcount (73%).
Hiring managers increasingly value non-technical attributes such as teamwork and problem-solving over hard technical skills. Yet, a skills-expectation gap remains: for example, cloud security is expected knowledge, but only 18% believe entry-level hires can actually execute on it.
These figures likely vary across sectors, regions, and role types. And to balance the narrative above, anecdotally, frustration still appears common among senior information security professionals, who often cite rigid hiring processes, bureaucratic delays, and limited budgets as persistent barriers.
Reports monitored: May 20 - June 30
To take a deeper dive in the topics most relevant for you, find below a list of all the monitored research reports (51) that were published during the observed period.
About
evisec's Cybersecurity Research Digest provides security leaders verified strategic insights via a carefully curated weekly summary of evidence-led, unbiased and objective cybersecurity research publications. Read more about our service here.
✉️ Suggestions or want to collaborate? Get in touch via LinkedIn or email (henry@evisec.xyz)




